In the 2022 Accelerate State of DevOps Report, more than 22 billion records were exposed because of data breaches. The lack of security that led to these data breaches would have been prevented through the introduction of security automation at every step, as more and more companies are learning. (Interestingly, the 2019 State of DevOps Report informed readers that “elite” teams deploy several times per day. It is perhaps a harbinger of the growing trend toward automated security, that by 2022 the Accelerate Report no longer reported on “Elite” teams, the standard for previous years.)
While every DBA and Dev team may want to move faster and be more agile, running faster isn’t necessarily wise if you’re doing so with limited vision. And the lack of DevSecOps automation has universally caused a few key fallout outcomes, including:
- DBAs have become the single point through which changes flow.
- Database professionals must prioritize integrity and security over the Devs need for speed.
- DBAs and database teams are frequently viewed through the lens of strict/rigid/slow data professionals who take too much time to deploy.
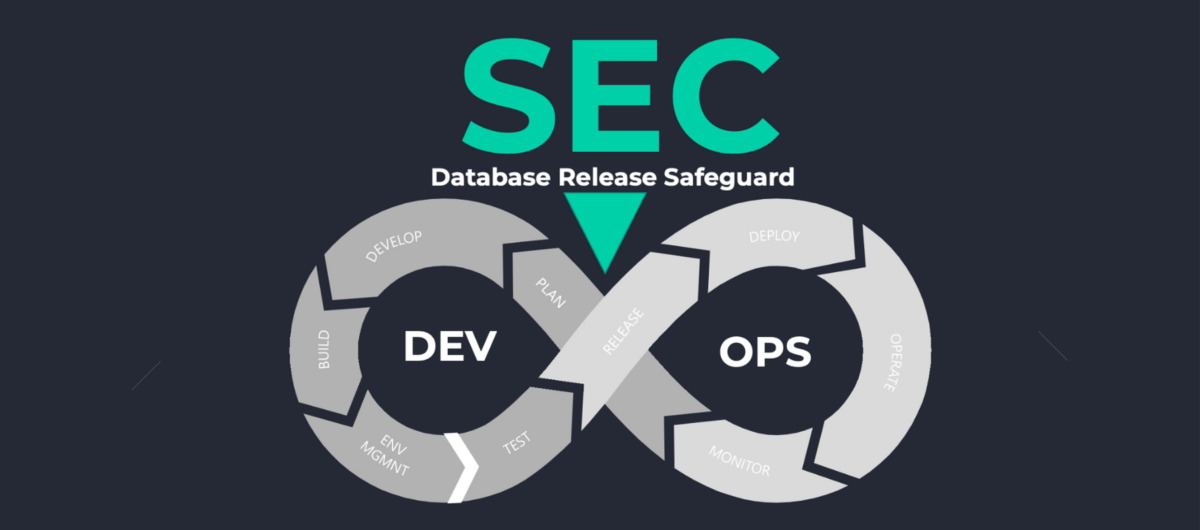
What is DevSecOps
DevSecOps is not primarily about setting up processes that combat operational errors. DevSecOps is about safe and secure collaboration across teams. Changes to the database are considered one of the riskiest and slowest processes in all of software development. Therefore, tried and true DevSecOps tools, ensuring database security compliance, is crucial.
The sheer magnitude and variety of tools, especially considering architectural variations, challenges database systems and environments to work coherently. Several teams working in silos, all handling different projects, often unaware of shared database elements, makes moving to corporate continuous integration and development a necessity.
A secure DevOps process requires increased team collaboration, extended beyond the development team. Data architects and DBAs must join forces with the security team and accumulate their value starting in the early changes design phase. While securing databases used to occur at the end of the development cycle, only reviewing and certifying after testing, continuous integration and deployment have removed that window. As a result, “DevSecOps” (a term credited to Neil MacDonald of Gartner in 2012) literally placed “security” in the middle of DevOps.
In 2019, with Dale Gardner, Neil MacDonald published “12 things to Get Right for Successful DevSecOps” where he offers the pragmatic advice that mechanization and DevSecOps automation tools are key to securing your data (e.g. #5 “Train developers on secure coding, but don’t expect them to be security experts”). Along those lines, #8 on his list is, “Implement stronger version control on all code and components.” This one step enables developers to check their changes in a common repository during the development process. It also ensures that everyone has the latest version of changes, as well as the “who,” “what” and “when” audit trail of all changes.
With a great source control tool for the database in place, continuous integration is possible, automatically testing changes at the point that they’re committed (and ensuring that they’re not breaking changes). Besides, if DBA and Dev teams are deploying scripts manually, it’s not only a threat to the system but an inefficient use of their time.
Five key takeaways that make “Sec” work
- A clear definition of roles and responsibilities… The common practice of granting access by login + password heavily increases corporate risk. Roles can be managed and access can be granted by specific responsibility (e.g. environment(s), database(s), schema/projects). Dedicating permissions to specific roles maximizes flexibility, but also ensures the user’s credentials always match what he or she is supposed to do – with a full audit trail.
- Making any change apparent, transparent and applicable to everyone is crucial. It avoids conflict and ensures the streamlining of database releases. It also enables, again, a full audit trail and monitoring of changes. This essential governance empowers all automation as well as safeguards the DB release processes.
- Applying a corporate “Sec” policy has never been easier. Using DevSecOps enables automated qualification of changes, made with secure automation, verifying that there is no violation of coding rules, policies and pre-identified practices.
- Dry-running the code first ensures that the broken code never actually gets to your database.
- The marriage of Source Control and DevSecOps for the database, means ending configuration drifts, partial updates, running a CI process to ensure changes can be implemented safely, and then releasing them to different environments.
How to implement database security
Implementing security and compliance should be done as early as possible in any automated or DevOps process. DevSecOps will enable you to make sure you can provide a secure application to your customers while assuring the quickest time to market and a well ironed-out process. Issues will either be prevented early or efficiently reported back to development with a short feedback loop. The overall process will become more secure, effective, and less costly due to the prevention of reworked solutions and reduced downtime.
DBmaestro helps companies make DevSecOps plans go live. Schedule a demo today